MARBLE MADNESS | Cybersicherheit
Video course: Preventing ransomware attacks
Video course: Preventing ransomware attacks
Couldn't load pickup availability
Course duration: Approx. 1 hour 25 minutes, flexible timing at any location
Invisible threats: Ransomware and keyloggers in focus
A live demonstration shows what ransomware and a keylogger can look like in action without causing any real damage. This gives course participants a direct understanding of how these threats work in the real world and why the defenses learned in the course are so important.
We are increasingly seeing an increase in ransomware attacks that encrypt both corporate and private user data. At the same time, so-called keyloggers are enjoying great popularity. These malicious programs secretly record keystrokes and transmit them to remote systems. This leads to the fundamental question: How is this even possible? How does this process work and how do hackers manage to create such software and use it on end systems to cause damage?
The consequences of ransomware attacks can be devastating. Companies can lose access to business-critical data, resulting in financial losses and a loss of reputation. Individuals can lose personal files, such as photos, documents and memories, which often cannot be recovered. Even if the demanded ransom is paid, there is no guarantee that the attackers will actually recover the data and this can lead to an endless extortion cycle.
The keylogger, on the other hand, is a sneaky threat that secretly records our keystrokes and steals sensitive information such as passwords, credit card numbers and personal messages. This type of malware can act silently and send sensitive data to criminals, which can lead to identity theft and financial loss.
The consequences of ransomware and keylogger attacks can be devastating. Companies can lose access to business-critical data, resulting in financial losses and a loss of reputation. Individuals are at risk of identity theft and misuse of personal information.
Our training aims to explain how to build a potential hacker environment from scratch. We start with a fresh Windows 11 system, develop a keylogger together and explain how it works using an easy-to-understand demonstration code. We then use the same environment to create a ransomware and demonstrate how to encrypt data. This allows us to gain insight into the dark side that remains hidden from most people.
After completing this training, you will have a better understanding of how criminal hackers might operate. You will understand what devastating damage these two demonstrations can cause in an emergency.
The duration of the training is approximately 1 hour and 25 minutes. During this time, you will gain a comprehensive understanding of how hackers can operate, how these attacks occur, and how you can potentially respond to them to protect yourself.
Contents:
-
Simulated ransomware attack:
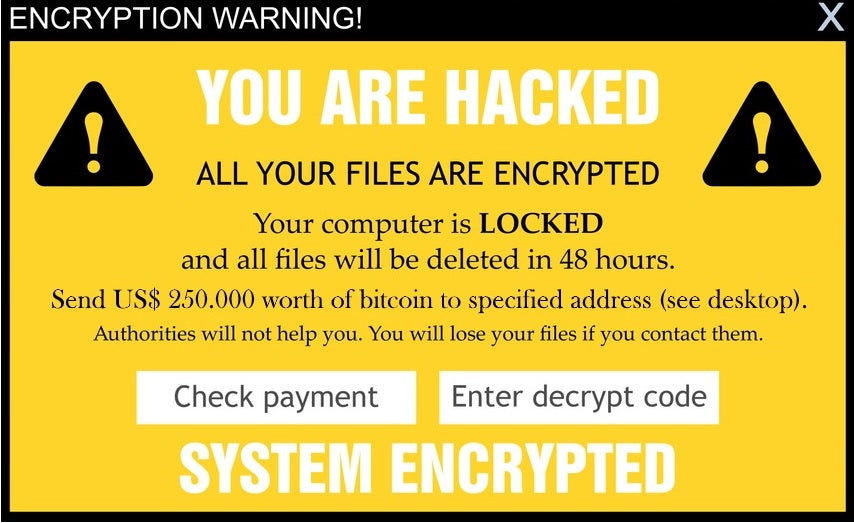
- Demonstration of a ransomware infection
- What happens if a device gets infected?
- What does a ransom demand look like?
-
Simulated keylogger attack:
- Demonstration of how a keylogger records keystrokes
- Visualization of the collected data
- Opportunities for abuse by cybercriminals
- Basic understanding of the system architecture:
- Structure of a possible hacker environment explained in detail
Requirements:
You do NOT need to be an expert to benefit from this course. Basic computer skills such as operating Windows or Apple, writing and saving texts, composing emails and logging into WiFi networks are sufficient as a basis.
Course duration: approx. 1 hour 25 minutes
Split